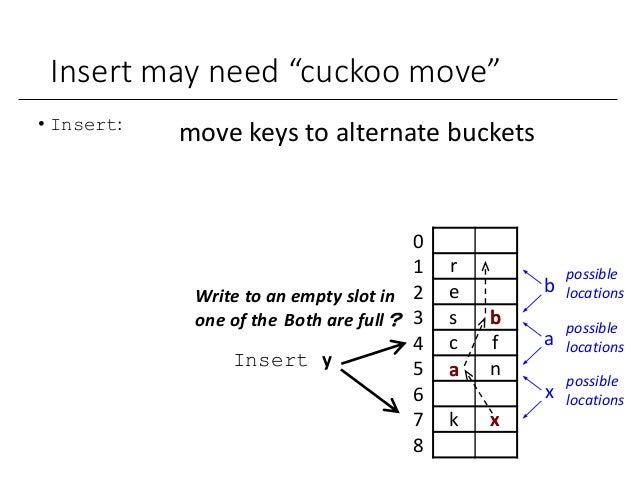
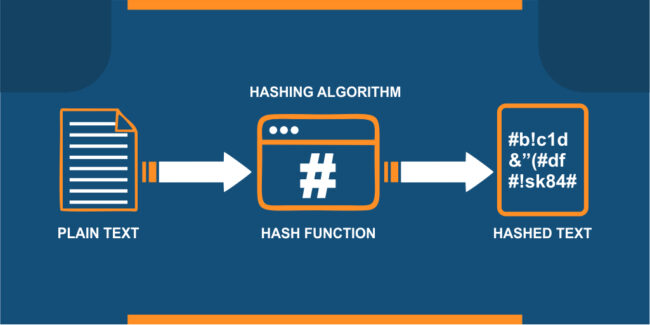
Nmap Weak Hashing Algorithm. The amount of information printed about the certificate depends on the verbosity level. This version of Apache has a number of known security issues, so as a tester you could research those to understand whether they are exploitable. If the "client to server" and "server to client" algorithm lists are identical (order specifies preference) then the list is shown only once. How to use the ssl-cert-intaddr NSE script: examples, script-args, and references. It records the discovered host keys in nmap.registry for use by other scripts. Output can be controlled with the ssh_hostkey script argument. Provide a guideline for the identification weak encryption or hashing uses and implementations. You may also compare the retrieved key with the keys in your known-hosts file using the known-hosts argument.
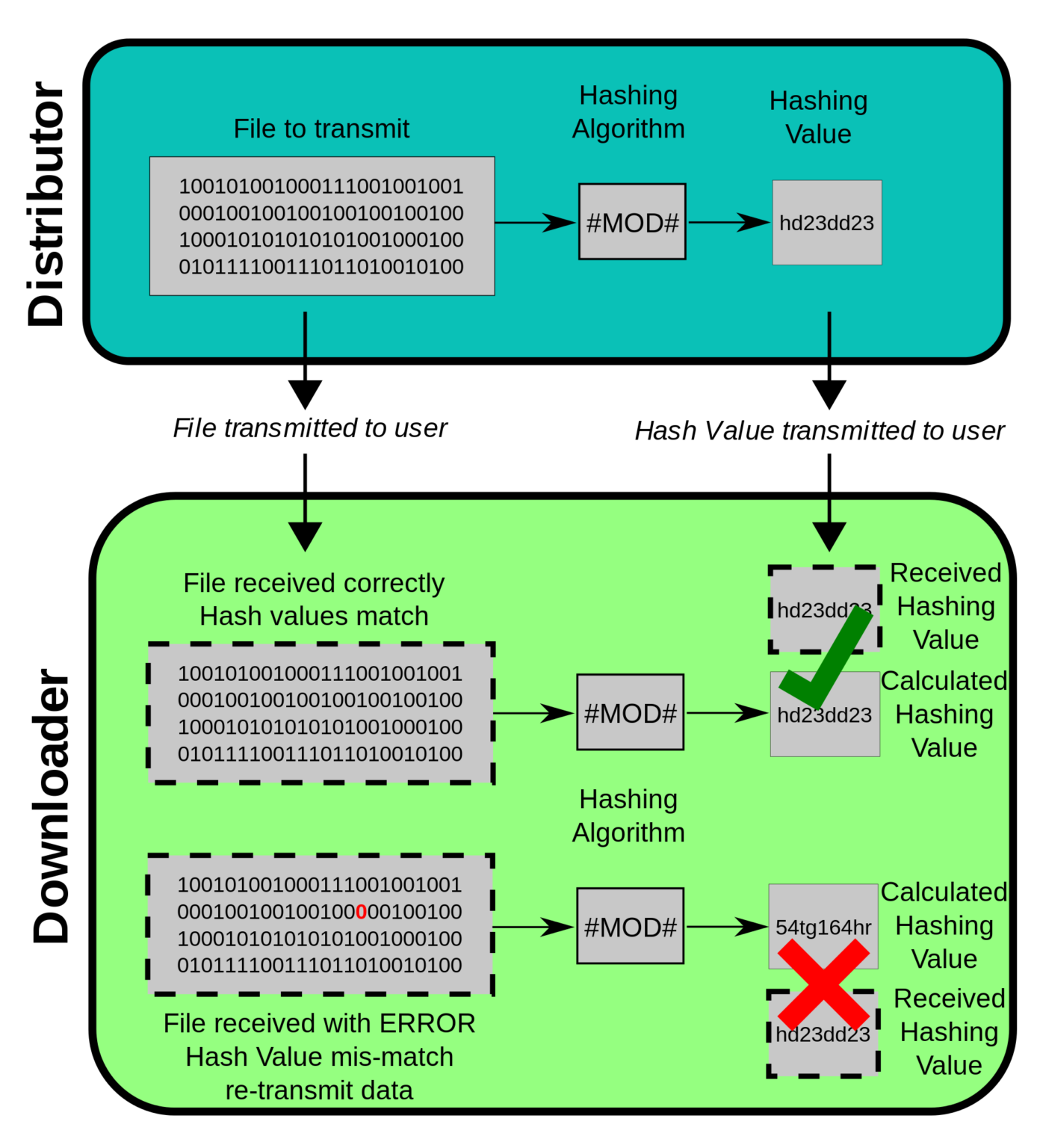
Nmap Weak Hashing Algorithm. Version of Apache used and the Operating system involved. Since the HashMap maintains a hard reference to the keys, the keys are still reachable and the WeakHashMap doesn't discard the entries. If the "client to server" and "server to client" algorithm lists are identical (order specifies preference) then the list is shown only once. Portal Home Knowledgebase PCI Testing SSL ports using nmap and check for weak ciphers Testing SSL ports using nmap and check for weak ciphers There is often the case where we can use the ssllabs to provide a list of weak ciphers used in the site. Port scanning is Nmaps core functionality but it also can be. Nmap Weak Hashing Algorithm.
More precisely, the presence of a mapping for a given key will not prevent the key from being discarded by the garbage collector, that is, made finalizable, finalized, and then reclaimed. public class WeakHashMap<K,V> extends AbstractMap <K,V> implements Map <K,V>.
Output can be controlled with the ssh_hostkey script argument.
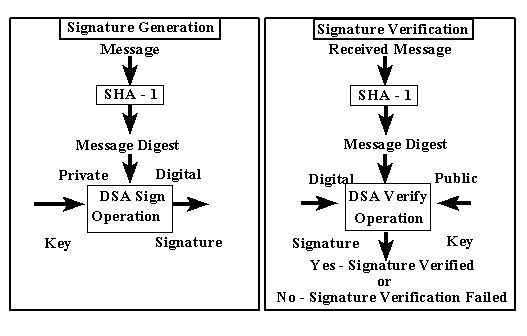
Nmap Weak Hashing Algorithm. An attacker can exploit this to generate another certificate with the same digital signature, allowing an. Port scanning is Nmaps core functionality but it also can be. If the "client to server" and "server to client" algorithm lists are identical (order specifies preference) then the list is shown only once. Additionally, it is important to observe that even strong hashing algorithms may not be suitable to hash passwords, in fact, password hashing algorithms have additional requirements: A hashtable-based Map implementation with weak keys. A cipher suite is specified by an encryption protocol (e.g.
Nmap Weak Hashing Algorithm.